STEP 1: CONFIGURING UTM
- Defining a user account
- Open Definitions & Users > Users & Groups > Users
- Click “New User” button
- Make the following setting:
- Username, Real name, Email address
- Authentication: Remote Access PPTP the “local” and “RADIUS” authentication methods are supported. With “local” authentication method, you will enter two fields password and repeat
- Click “Save”
- Configuring L2TPOver IPsec settings
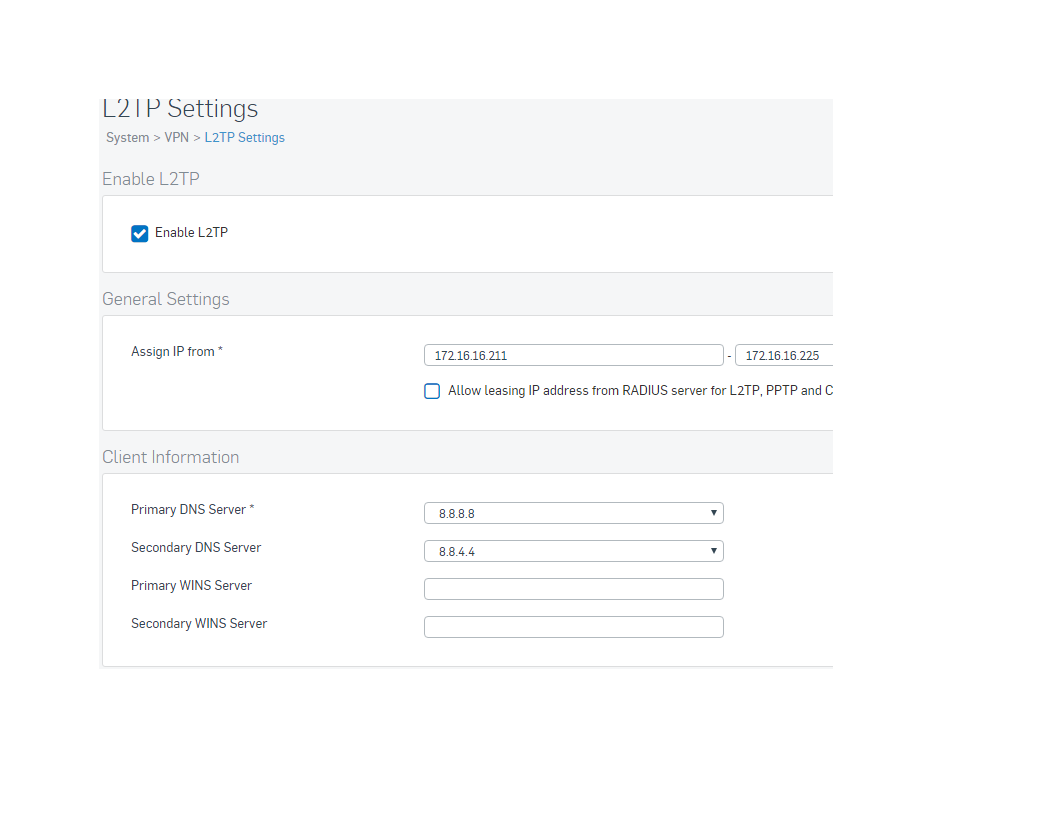
- Open Remote Access > L2TP Over IPsec > Global tab
- Enable L2TP
- Make the following settings:
- Interface: Select the network interface to use for L2TP access.
- Authentication mode: Select the authentication mode (Preshared key or X.509 CA Check)
- Preshared key: enter the shared secret. This is secure phrase or password that is used to set up the secure tunnel.
- X.509 CA Check:
Certificate: Select the local X.509 certificate to authenticate the server.
- Assign IP addresses by: Select IP address pool or DHCP Server
- IP address pool: default IP address 10.242.1.x/24, Network is called VPN Pool (PPTP). D
- DHCP server (DHCP server Via interface)
- Authentication via: Select authentication method “local” or “RADIUS”
- Users and groups: When you using local authentication, please select the users or groups that should be able to use PPTP remote access.
- Click Apply to save your settings
- Configuring Advanced L2TP over IPsec settings
- Open Remote Access > L2TP over IPsec > Debug tab
- IKE Debugging
- Control Flow: Displays control messages of IKE state
- Outbound Packets: Displays content of outgoing IKE messages
- Inbound Packets: Displays content of incoming IKE messages
- Kernel Messaging: Displays communication messages with the Kernel
- High Availability: Displays communication with other HA nodes
- Click Apply to save your settings
- Optionally, enable debug mode => click Apply
- Defining Firewall Rules
- Open Network Protection > Firewall > Rules tab
- Click “New Rule button “
- Make the following settings:
- Sources: Add the remote host or user
- Services: Add the allowed services
- Destinations: Add the allowed networks
- Action: Select Allow
- Click Save
- Enable the rule: clicking the status icon => status icon turns green
- Defining Masquerading Rules
- Open Network Protection > NAT > Masquerading tab
- Click New Masquerading Rule button

- Make the following settings:
- Network: Select network of the remote endpoint.
- Interface: Select interface.
- Use address: If the interface you selected has more than one IP address assigned, you can define here which IP address is to be used for masquerading
- Click Save
- Enable rule
- Optionally, activate the proxies
STEP 2: CONFIGURING REMOTE CLIENT
The Layer Two Tunneling Protocol (L2TP) enables you to provide connections to your network through private tunnels over the internet. The firewall supports L2TP as defined in RFC 3931. Note To activate a connection, you must first enable L2TP. Click Show VPN settings and click the L2TP tab. To create the L2TP connection, do as follows: Turn on L2TP VPN connections, and specify your settings. Create your L2TP policy. Create a firewall rule to allow inbound VPN traffic. Yeah I'm really surprised there's no generic template to download for XG. One of those head-scratching missing puzzle pieces on XG. I guess that's what I get for being an early adopter (despite what Sophos like to claim I still consider V17 pretty early adoption). After testing on the weekend, I'm going to deploy IPSEC over L2TP for now.
Allow leasing IP address from RADIUS server for L2TP, PPTP, and Sophos Connect client When users are authenticated using a RADIUS server, use the IP address provided by the RADIUS server. If the RADIUS server provides no addresses, XG Firewall assigns the static address configured for the user or leases an address from the specified range.
- Start your browser and open the User Portal => Log in to the User Portal => go to Remotes Access lab => view information L2TP Over IPsec (can review “preshred key”).
- Configuring Windows Client
- Click Start => Control Panel
- In the Control Panel, click Network and Internet => Network and Sharing Center => Set up a new connection or network
- Define the dial-up Internet connection
.jpg)
- Click Next
- Enter the hostname or the IP address of the gateway => Allow other people to use this connection
- Click Next
- Click Create
- Right-click the new connection and select Properties => Security => make information same picture follow:
- click OK
- Open Network => enter username and password => Connected
Done, Thanks you!
You can configure IPsec remote access connections. Users can establish the connection using the Sophos Connect client.
Introduction
The Sophos Connect client allows you to enforce advanced security and flexibility settings, such as connecting the tunnel automatically. To configure and establish IPsec remote access connections over the Sophos Connect client, do as follows:
- Configure the IPsec remote access connection.
- Send the configuration file to users.
- Add a firewall rule.
- Send the Sophos Connect client to users. Alternatively, users can download it from the user portal.
Users must do as follows:
- Install the Sophos Connect client on their endpoint devices.
- Import the configuration file into the client and establish the connection.
Configure IPsec (remote access)
Sophos Xg L2tp Not Working
- Go to VPN > IPsec (remote access) and click Enable.
- Specify the general settings:
Name
Setting
Interface
Select a WAN port.
Authentication type
Specify a preshared key or the local and remote certificates.
Local ID
Remote ID
Specify the IDs if required.
Allowed users and groups
Select the users and groups you want to allow.
- Specify the client information. The following settings are an example:
Name
Setting
Name
TestRemoteAccessVPN
Assign IP from
192.168.1.11
192.168.1.254
DNS server 1
192.168.1.5
- Specify the advanced settings you want and click Apply.
Name
Setting
Permitted network resources (IPv4)
LAN_10.1.1.0
DMZ_192.168.2.0
Send Security Heartbeat through tunnel
Sends the Security Heartbeat of remote clients through the tunnel.
Allow users to save username and password
Users can save their credentials.
Netbarrier x9. NetBarrier X9 Details Active application list easily identifies applications using bandwidth as well as incoming vs. Outgoing bandwidth for each application Logical default profiles for the different kinds of networks you connect to (home, public, and work). Number 1 Leading Mac security and antivirus software since 1997. Award-winning AV, network security, utility and parental control software exclusively for Mac OS X and macOS. New articles New articles and comments. ★ NetBarrier X9 User Manual. ★ About NetBarrier X9 Alerts. How To Disable the NetBarrier Application Monitor Window. How To Temporarily Disable (Turn Off) NetBarrier Protection. How to Reset NetBarrier. NetBarrier X9 Active application list easily identifies applications using bandwidth as well as incoming vs. Outgoing bandwidth for each application Logical default profiles for the different kinds of networks you connect to (home, public, and work).
- Click Export connection.
The exported tar.gz file contains a .scx file and a .tgb file.
- Send the .scx file to users.
- Optional To assign a static IP address to a user connecting through the Sophos Connect client, do as follows:
- Go to Authentication > Users, and select the user.
- On the user's settings page, go down to IPsec remote access, click Enable, and enter an IP address.

